Splunk Staging & Security
Seamlessly Prepare, Protect, and Index Data
Wrangle, Secure and Index Data for Splunk Seamlessly
Splunk is a robust analytic tool for a variety of data sources. However, Splunk cannot ingest dark data in a comprehensive way, and it lacks the kinds of data protection capabilities that compliance-minded data scientists require. With IRI software and Splunk combinations like these, you can do a lot more:
1. Index Splunk Immediately With Prepared and Protected Data
Using either the Splunk Universal Forwarder with IRI Voracity, or the IRI Voracity Data Munging and Masking App for Splunk, you can leverage the extremely fast data wrangling and de-identification capabilities of IRI Voracity and the visual analytics and actions you can take on that data with Splunk. Integrate, cleanse, and anonymize huge, raw data sets in a variety of formats and index them in Splunk immediately, through memory.
2. Prepare Unstructured Data Sets for Splunk
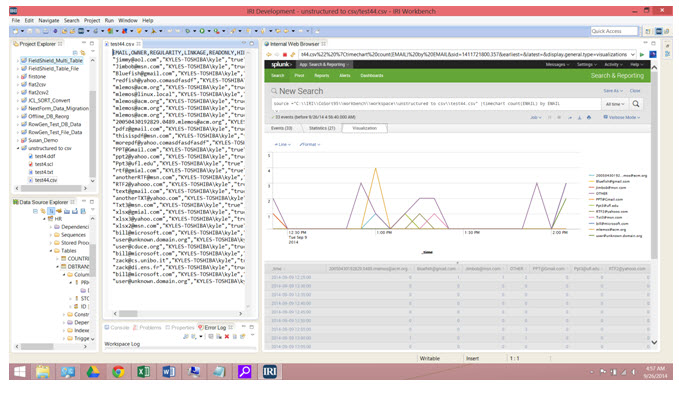
The dark data discovery wizard in the IRI Workbench GUI can search and structure data in MS Office documents, email repositories, and .pdf, .rtf, and .xml files all at once. It can also discover forensic metadata about each data source with an element matching the user's search pattern(s).
The resulting flat file contains all the data (and optional metadata) results, which Splunk can index easily ... and even display in the same GUI with your data preparation and management activities:
3. Protect Data for Splunk, With or Without Reversibility
Splunk has identified a number of data encryption scenarios, but it does not offer the format-preserving encryption of IRI FieldShield (available in the same GUI above or as part of a Voracity subscription) that maintains realism for data entering or referential integrity for data leaving. Use the IRI add-on for Splunk to run a FieldShield (or IRI RowGen test data generation) job script to index this data into splunk as it is protected (or produced).
Because IRI data masking functions are at the field level, they are more secure; if (unlike Splunk) an encryption key is disclosed, other fields with other keys or algorithms are still safe.
4. Send IRI Data Security Software Logs to Splunk
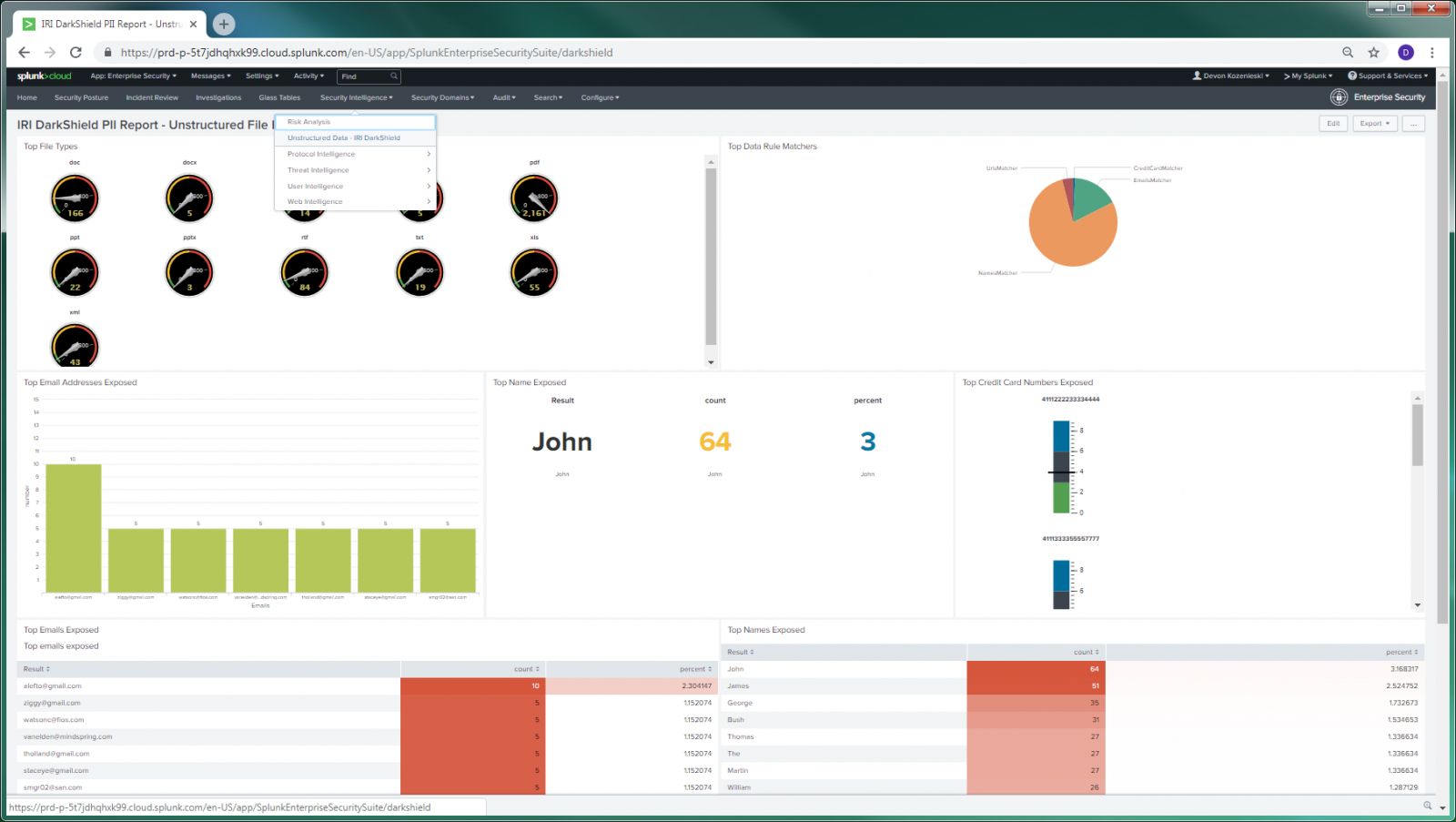
In addition, all IRI static data masking products -- FieldShield, DarkShield, and CellShield EE -- can produce audit trail output suitable for Spunk Enterprise Security (ES) SIEM/ SOC environments. This includes the ability to create adaptive responses and Splunk Phantom playbooks to take direct action on the identified data.
See this press release for links to articles on how to display and act on data from IRI products like DarkShield in Splunk! Here is an example of Splunk ES visualizing DarkShield dark data search and masking logs: